Cloud services have become ever more popular as there are many benefits such as fast deployment, pay-as-you-go, no device purchasing, no environment changing, no software installation, and no websites changing. As more and more enterprises are migrating their core businesses to the cloud and building their own private or hybrid cloud to provide application services, it seems that cloud information security has become an essential module for cloud deployment.
Digital transformation has become the main method for enterprises to pursue growth and react to the volatile environment, and thus websites has also become an important channel to approach customers and vendors, providing borderless service introductions, inquiries, sales and transactions and corporate image-building anytime, anywhere. However, any information that is disclosed on public internet is exposed to information security risks such as malfunction caused by attacks, data theft or tampering, and redirection to malicious websites, which would harm corporate operation and image. It is especially critical for e-commerce as home economy has grown exponentially and consumers now spend most of their time shopping on websites; if the websites are hacked or attacked by ransomware, resulting in the leakage of a huge amount of transaction information, it will damage both the revenue and the reputation of the corporate so it is not to be ignored.
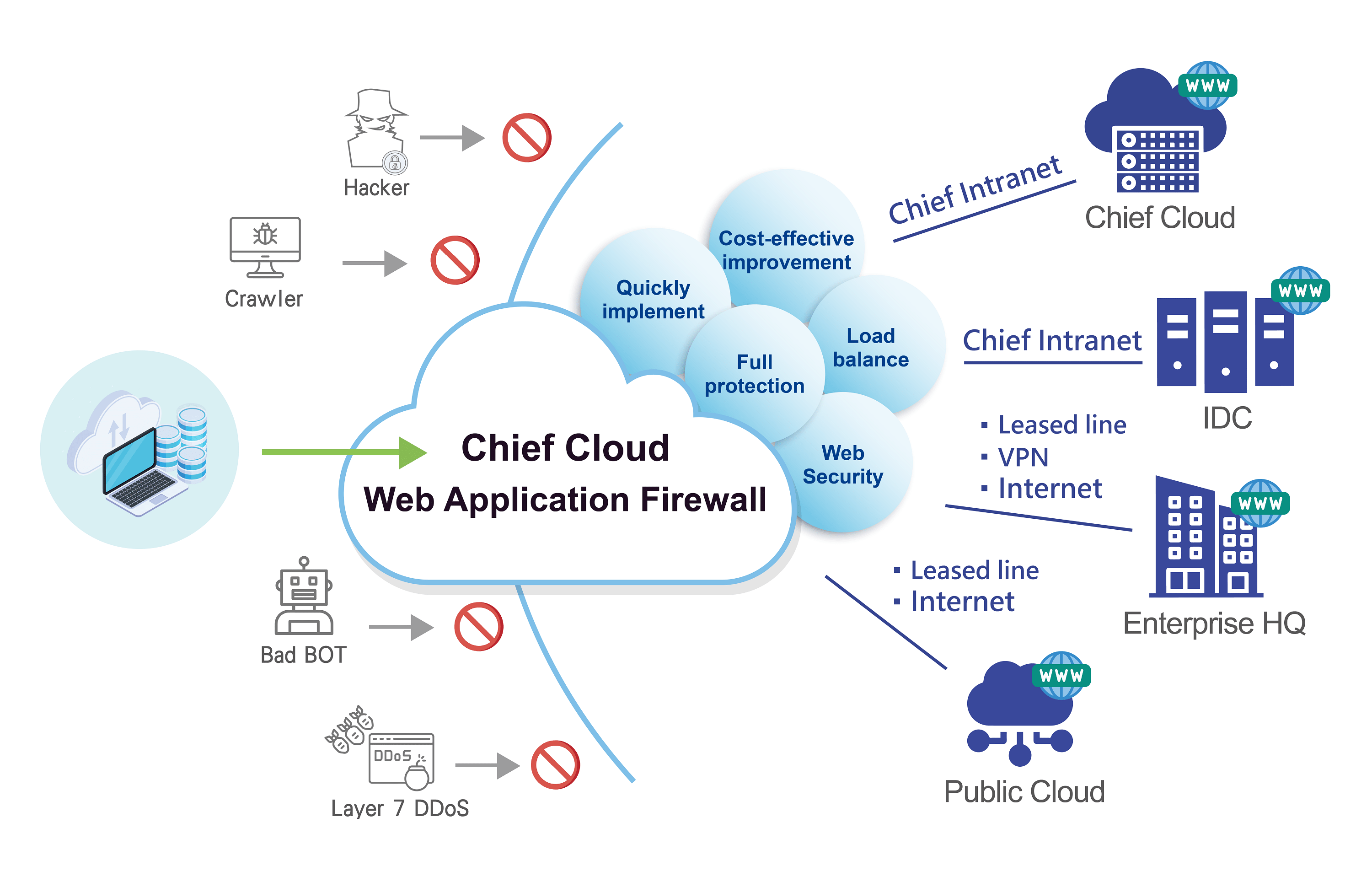
The Cloud Information Security Integrated Application Service provided by Chief Telecom is structured in Chief Telecom’s Internet Datacenter (IDC) and equipped with the core technology of world-renowned F5 to provide Cloud Web Application Firewall Service, allowing customers to easily deploy cloud architecture solutions that meet the enterprise information security standards. Customers are able to enjoy an international-grade information security services on a monthly subscription basis, with services ranging from load balancing, bat robots identification, web crawler defense, Layer 7 DDoS attack defense, API anomaly detection, to other common information security issues, which not only protects the enterprises from OWASP Top 10, but also enables them to confidently enjoy the benefits brought by the website services.